IT Security Standards Kit

IT Security Standards Kit
What are important IT security standards? What are useful ways to implement cyber security and how to prepare for a Cybersecurity Audit according IEC, NIST, ISO27001:2013 standards? Download this IT CyberSecurity Kit? Download this IT standards kit now.
- IT Security Gap Analysis
- IT Security Audit Checklist
- Data Backup Plan
- Data Security
- Security Incident Management
- Vulnerability Management
- User Access
- Logging and Monitoring
- Cloud Computing Security
- IT Asset Management
- Change Management
- IT System Acquisition & Development
- Web Application Security
- Physical Security
- Bring Your Own Device BYOD
- End-User Protection
- Network Security
- IT Recovery
- Information Security Risk & Compliance Management
- Human Resources Security
- IT Acceptable Use
- Third-Party Risk Management
- Secure Algorithm List
- Data Classification Standard
- Etc
IT Security Roadmap
How to implement CyberSecurity in your organization? What are the ways to implement cyber security? Download this IT Standards Roadmap if you are working on IEC, NIST, ISO27001:2013 or other control objectiv
- Set goals, which IT Security standard according organizational goals and data security
- Gain insights into the meaning and impact of IT Security
- Gain insights into IT Security vs GDPR/CCPA similarities and differences
- Perform high-level IT Security compliance check
- Perform gap assessment
- Gain senior management commitment
- Initiate a project with appropriate resources and budget
- Establish document control
IT Security Initiation, Roles, awareness and training
- Create the Project Charter
- Define IT security roles and responsibilities
- Identify Lead Data Protection Supervisory Authority
- Recruit Information Protection Officer (if required)
- Appoint Information Protection Officer (if required)
- Conduct IT security competence and training needs assessment
- Perform IT security-related training and familiarisation
- Conduct IT security and information security awareness training
Planning
- Conduct initial personal information gathering exercise
- Perform audit of personal information by business area
- Define or Amend Data Security Policy
- Identify a lawful basis for processing personal information in each case
- Conduct legitimate interest assessments where required
- Identify record-keeping requirements and procedures
- Identify and dispose of Irrelevant Personal Information and keep a log
Execution and Control
- Define personal information retention and protection policy
- Create or amend existing privacy notices
- Review and amend consent methods and procedures
- Address age-related consent and controls (children)
- Create or amend response to unsuccessful subscribers
- Create or amend response to deletion request of consumers
- Create or amend Data Classification Standard
- Create or amend Data Backup Plan
- Define or amend Data Security Policy
- Create or amend Security Incident Management
- Create or amend Vulnerability Management
- Create or amend User Access standard
- Create or amend Logging and Monitoring
- Create or amend Cloud Computing Security
- Create or amend IT Asset Management
- Create or amend Change Management
- Create or amend IT System Acquisition & Development
- Create or amend Web Application Security standard
- Create or amend Create or amend Physical Security
- Create or amend End-User Protection
- Create or amend Network Security
- Create or amend IT Recovery
- Create or amend Information Security Risk & Compliance Management
- Create or amend Human Resources Security
- Create or amend HR Employee Confidentiality Statement
- Create or amend IT Acceptable Use
- Create or amend Third-Party Risk Management
- Secure Algorithm List
Data subject management
- Create and implement data subject request procedures
- Create and implement data subject consent withdrawal form
- Create and implement parental consent withdrawal form
- Start recording data subject requests
- Create and implement User Deletion Request Policy
- Create and implement Data Subject Access Request Form
Controllers and processor
- Update contracts with processors to be IT Security compliant
- Distribute supplier questionnaires regarding personal information protection
- Provide information to controllers for whom we act as a processor
- Update contracts with controllers to be IT Security compliant
- Address employee confidentiality requirements
- Create and implement Bring Your Own Device Policy
Data protection impact assessment
- Define the data protection impact assessment process
- Conduct data protection impact assessment training
- Perform initial data protection impact assessment
International transfers
- Identify international transfers of personal information
- Assess the legality of existing international transfers
- Put in place agreements for international transfers of personal information (where required)
Personal information breach management
- Create information security incident management procedure
- Create information security incident management register
- Create personal information breach notification procedure (Data Subjects)
- Create personal information breach notification procedure (Supervisory Authority)
- Conduct information security incident management training
- Test incident management and breach notification procedures
- Create business continuity plan or disaster plan in case of crisis
- Inform the data subjects that were exposed to a data breach
Project closure
- Repeat gap assessment to identify remaining non-compliant areas
- Respond to complaints of data privacy breaches, etc
- Address any remaining non-compliant areas
- Perform post-project review
- Cryptography – Encryption and hashing solutions for protecting sensitive data when in transit or storage, and
- Data Masking – Data masking is a technology for obscuring sensitive information in non-production environments. Through data masking [Company Name] protects the content of sensitive data in non-production environments to ensure that:
- Application developers, testers, privileged users and outsourcing vendors do not have unauthorized access to such information.
- The data maintains the referential integrity of the original production data.
Check out our collection with newly updated IT Security Kit Standards templates (Microsoft Word, Google Docs, Microsoft Excel, Google Sheets, PowerPoint, Google Slides) including policies, controls, processes, checklists, procedures and other documents. The full list of documents, organized in line with the ISO/IEC 27001:2013/17/etc standard are listed below:
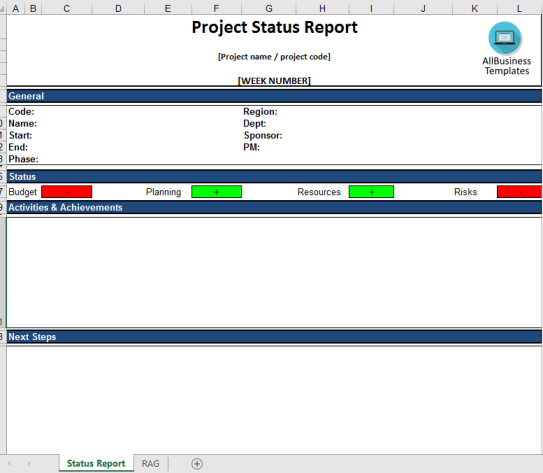
Project Status Report Excel template
Are you looking for a way to easily collect project results? Check out this report. It is free from any protection and can easily be edited to your needs.
Cyber Security Incident Report template
How to create a professional Cyber Security Incident Report? Download this Cyber Security Incident Report template now!
IT Service Level Agreement
How to create an IT Service Level Agreement? Download this It Service Level Agreement template now!
GDPR Data protection policy
Are you looking for this GDPR Data protection policy sample? Is your organization GDPR ready? Download this GDPR Data protection policy now
Security Audit Checklist
How to perform a professional Security Audit? How to create a Security Audit Checklist? Download this Security Audit Checklist template now!
IT Security Policy Government Example
How to draft a Policy for the IT Security of your organization? An easy way to start implementing IT Security is to download this Information Security Policy te
Cyber Security Incident Report
How to create a Cyber Security Incident Report? What information must be included in an incident report regarding an incident or error? Download this Cyber Security Incident Report template now!
Security Risk Management Plan
Are you looking for a professional Security Risk Management Plan? Download this Security Risk Management Plan if you are working on IEC, NIST, ISO27001:2013
Security Threat Assessment
How to create a Security Threat Assessment? Download this Security Threat Assessment template now!
Security Service Level Agreement Template
How to create a Security SLA? Download this Security Service Level Agreement template that will perfectly suit your needs!
IT Security Training Policy
How to create an IT Security Awareness Training Policy for your organization? Download this government IT Security Training Policy if you are working on IEC, NI
Security Incident Report
Are you looking for a professional Security Incident Report? If you've been feeling stuck or lack motivation, download this template now!
HIPAA Security Incident Report
How to create a Hipaa Security Incident Report? Download this Hipaa Security Incident Report if you are working on IEC, NIST, ISO27001:2013 or other IT and Cybe
GDPR Bring Your Own Device Policy BYOD
How to draft a BYOD policy? Are you looking for this Bring Your Own Device Policy (BYOD) Policy? Download this fit-for-purpose Bring Your Own Device Policy Policy now!
GDPR Supplier Data Processing Agreement
Are you looking for this Supplier Data Processing Agreement? Download this Supplier Data Processing Agreement now!
IT Security Roadmap
How to implement CyberSecurity in your organization? What are the ways to implement cyber security? Download this IT Standards Roadmap if you are working on IEC, NIST, ISO27001:2013 or other control objectiv
IT Security Standards Kit
What are important IT security standards? What are useful ways to implement cyber security and how to prepare for a Cybersecurity Audit according IEC, NIST, ISO27001:2013 standards? Download this IT CyberSecurity Kit? Download this IT standards kit now.
Data Security Plan
How to create a Data Security system? Download this Data Security plan if you are working on IEC, NIST, ISO27001:2013 or other IT and Cyber Security Standards and control o
IT Security Disaster Plan
How to create an IT Security Disaster Plan? Download this IT Security Disaster Plan if you are working on IEC, NIST, ISO27001:2013 certification.
Internal IT Security Gap Analysis
How to do an internal analysis of the IT Security status of your organization? Download this Internal IT Security Gap Analysis
Logging and Monitoring IT Standard
Download this Logging and Monitoring IT Standard if you are working on IEC, NIST, ISO27001:2013 or other IT and Cyber Security Standards and control objectives.
IT Recovery Standard
How to create an IT Recovery Standard for your organization? Download this IT Recovery Standard if you are working on IEC, NIST, ISO27001:2013 or other IT and C
End User Protection IT Standard
How to write an End-User Protection Standard? Download this End User Protection IT Standard if you are working on IEC, NIST, ISO27001:2013 or other IT and Cyber
Vulnerability Management IT Security Standard
How to create a Vulnerability Management IT Security Standard for your company? Download this Vulnerability Management CyberSecurity standard now.
Cloud Computing IT Security Standard
Download this Cloud Computing CyberSecurity Standard if you are working on IEC, NIST, ISO27001:2013 or other IT and Cyber Security Standards and control objecti
Data Backup Plan
How to create a Data Backup Plan to improve your IT Security? Download this Data Backup Plan Standard if you are working on IEC, NIST, ISO27001:2013 or other IT
Security Incident Management IT Standard
How to create a Security Incident Management Standard for your IT organization? Download this Security Incident Management if you are working on IEC, NIST, ISO2
IT Asset Management Cybersecurity Standard
How to create an IT Asset Management System for your organization? Download this IT Asset Management Standard if you are working on IEC, NIST, ISO27001:2013, or
Change Management IT Cybersecurity Standard
How to create a Change Management CyberSecurity standard for your organization? Download this IT Security Standard now Standards and control objectives
IT System Acquisition & Development
How to create an IT System Acquisition & Development Standard? Download this IT System Acquisition Standard if you are working on IEC, NIST, ISO27001:2013, etc
Physical Security IT Standard
How to create a Physical Security Standard for IT Assets? Download this Physical IT Security if you are working on IEC, NIST, ISO27001:2013, or other IT and Cyb
Network Security IT Standard
Download this Cybersecurity standard for Network Security if you are working on IEC, NIST, ISO27001:2013 or other IT and Cyber Security Standards and controls
IT Security Risk & Compliance Management
How to create an Information Security Risk and Compliance Management Standard? Download this IT Information Security Risk & Compliance Management Standard now.
Human Resources IT Cybersecurity Standard
How to create a Human Resources IT Cybersecurity Standard for your company? Download this HR IT Security Standard model if you are working on IEC, NIST, ISO2700
Third Party Risk Management Standard
How to create a Third-Party Risk Management Standard for your IT organization? Download this Third-Party Risk Management if you are working on IEC, NIST, ISO270
Secure Algorithm List IT Security Standard
How to create a Secure Algorithm List for IT organization? Download this Secure Algorithm List if you are working on IEC, NIST, ISO27001:2013 cybersecurity.
Acceptable Use IT CyberSecurity Standard
How to define an Acceptable Use IT CyberSecurity Standard? Download this Acceptable Use IT Security Standard template if you are working on IEC, NIST, ISO27001:
Employee Confidentiality Statement IT Security
How do you write a confidential statement? Download this Employee Confidentiality Statement if you are working on NIST, Cyber Essentials (UK), ISO/IEC 27001:201
Statement Of Applicability CyberSecurity
How to create a Statement Of Applicability according CyberSecurity standards? Download this Statement Of Applicability if you are working on IEC, NIST, ISO27001:2013 or other IT and CyberSecurit
CyberSecurity Analyst Job Description
What is a CyberSecurity Analyst? Are you looking for a CyberSecurity Analyst Job Description? What are the important details in a CyberSecurity Analyst Job Desc